BYOD
I’ve spent a good part of the last year working on mobile strategy, so I get asked a lot about Bring Your Own Device (BYOD[1]). This is going to be one of those roll up posts, so that I can stop repeating myself (so much).
It’s not about cost (of the device)
A friend last week sent me a link to this article ‘2013 Prediction: BYOD on the Decline?‘. My reply was this:
News at 11, an unheard of research firm gets some press for taking a contrarian position. They ruined it for themselves by trying to align BYO with cost savings. Same schoolboy error as cloud pundits who think that trend is about cost savings.
Cloud isn’t about cost. It’s about agility.
BYOD also isn’t about cost. It’s about giving people what they want (which approximately equals agility).
In fact cloud and BYOD are just two different aspects of a more general trend of the commoditisation of IT; cloud deals with the data center aspects, and BYOD with the end user devices that connect to services in the data center[2].
The enterprise is no longer in the driving seat
When I was growing up the military had the best computers, which is a big part of why I joined the Navy. Computers got cheaper, and became an essential tool for business. For a time the enterprise had the best computers, which is why I left the Navy and found work fixing enterprise IT problems. Now consumers have the best computers – in their pockets; time for another career change.
There are a number of companies out there trying to sell their device/platform or whatever based on it have ‘enterprise security’ features. This is a route to market that has failed (just take a look at the RIM Playbook) and will continue to fail because the Enterprise doesn’t choose devices any more.
- Consumers choose devices
- Employees take their consumer devices to work
- Devices that come to work need applications to make them more useful
Even when the Enterprise is buying devices, because the trade off between liability and control is worth it, they’ve buying the same devices that employees would choose for themselves.
MAM is where the action is, MDM is a niche
For a consumer device to be useful in a work setting it needs access to corporate data, and in most cases there is a need/desire to place controls around how that corporate data is used. There are essentially two approaches to doing this:
- Mobile Application Management (MAM) – where corporate data is secured in the context of a single application or a group of connected applications (that may share policy, authentication tokens and key management). With this approach the corporate data (and apps that manage it) can live alongside personal apps and data.
- Mobile Device Management (MDM) – where corporate data is secured by taking control (via some policy) over the entire device. This is how enterprises have been dealing with end user environments for a long time, but that was usually a corporate owned device (where this approach may still be appropriate) rather than BYO. Most users are bringing their own device to work to escape from the clutches of enterprise IT (and what the lawyers make them do), so MDM is a bad bargain for the employee. It’s also a minefield for the enterprise – what happens if employee data (e.g. precious photos) are wiped off a device? Could personal data (maybe something as simple as a list of apps installed) be accessed by admins and used inappropriately?
There is a 3rd way – virtual machine based segregation – but that approach is mostly limited to Android devices at the moment, and anything that ignores the iOS elephant in the room isn’t inclusive (and thus can’t be that strategic).
MAM isn’t without its issues, as it is essentially a castle in the air – an island of trust in a sea of untrustworthiness. This will eventually be sorted out by hardware trust anchors; but for the time being there must be some reliance on ecosystem purity (can Apple etc. keep bad stuff out) and tamper (jailbreak) detection[3].
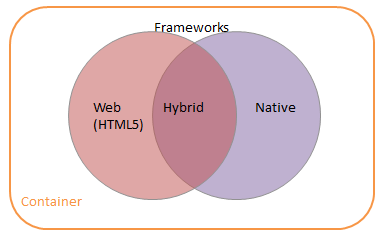
Application Frameworks
The containment of corporate data is one issue, but regardless of whether that’s done at the app level with MAM or the device level with MDM enterprises also need to figure out how to get that data into an application. There are essentially three approaches:
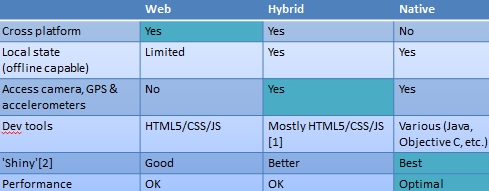
- Thin Client – rather than make a new app for mobile, just project out an existing application and access it via the tablet/smartphone or whatever. This can be pretty awful from a user experience point of view as the approach depends on good network connectivity, and often does a bad job at presenting apps designed for keyboard and mouse to a device that offers touch and gestures. It is however a quick and relatively easy way of preserving an existing investment in line of business applications. The connectivity issues can be dealt with by using protocols that are better optimised for mobile networks (such as Framehawk), and it’s also possible to use UI middleware to refactor desktops apps for the BYO user experience.
- Mobile Web – take an existing web site and provide a mobile version of it, reusing as much of the existing content management and UI componentry as possible. This is usually a great approach for cross platform support, but doesn’t give the shiniest native experience (and performance can be poor).
- Native App – build something specific for a given target platform for the best user experience and performance. This can be perceived as an expensive approach, though getting mobile apps (which are after all just the UI piece of what’s usually a much larger app ecosystem) developed can be small change compared to other enterprise projects.
It’s also possible to hybridise 2&3, though this involves trade offs on performance and flexibility that need to be carefully considered. Hybrid should not be a default choice just because it looks like it covers all the bases (just look at Facebook backing out of their hybrid approach).
Conclusion
BYOD may presently look like a trend, but it isn’t some temporary fad. It’s an artefact of consumer technology transforming the role of IT in the enterprise. That transformation places demands on IT that broadly fall into two areas: containment (of sensitive data) and frameworks (to develop apps that use/present that data). MAM is the most appropriate approach to containment for BYOD, and frameworks should be evaluated against specific selection criteria to determine the right approach on a case by case basis.
Notes
[1] It’s remarkable how quickly the conversation moved on from Bring Your Own Computer (BYOC) to Bring Your Own Device (BYOD) – normally meaning a tablet, but usually expanded to include smartphones that support similar environments to tablets.
[2] At some stage in the (not that distant) future the cloud will invert, and be materially present at the edge, on the devices that we presently consider to be mere access points.
[3] For the time being things are much easier in the iOS ecosystem, which is going to get problematic when all of those shiny new Android tablets that people get for Christmas show up in the New Year.
Filed under: technology | Leave a Comment
Tags: android, architecture, BYO, BYOC, BYOD, iOS, iPad, iphone, mobile, smartphone, strategy, tablet
No Responses Yet to “BYOD”