Persona
OK, it’s time for my first serious post, and it’s not about a brand of fertility monitor.
Persona is a term that’s increasingly being used in conversations around digital identity, but it’s not one that I typically find to be well defined. The Wikipedia entry doesn’t help much, as it is about the more general definition of persona as ‘a social role’. When I checked the Identity Gang glossary (or Identipedia) the last time I was looking for help that didn’t help either, though I now see that there are a number of definitions there (I can’t decide whether this is better or worse than none at all). The discussion about Limited Liability Persona is getting some more traction in the aftermath of the Scoble/FaceBook debacle, but that concentrates on a proposed legal framework and the underlying definition of persona is somewhat implicit.
The purpose of this post is to put forward my own definition, and hopefully by eliciting some comments it will be possible to find some sort of consensus definition.
It is my contention that persona is an abstraction between an entity (usually a biological entity, or person) and a bundle of one or more digital identifiers, so that the entity can present themselves differently according to context. This is similar to using a role as an abstraction between a digital identifier and a bundle of privileges (though I’m increasingly leaning towards attribute based access control [ABAC] in favour of role based access control [RBAC] as role management is a deep and sticky tar pit).
At this stage it’s usually helpful to offer some examples:
-
‘Blogger’ – my persona of ‘blogger’ associates with my digital identity (OpenID) ‘thestateofme.wordpress.com’, which in turn places me in the role of ‘author’, which gives me the privilege to ‘post’, ‘approve comments’ etc.
-
‘Web surfer’ – my persona of ‘web surfer’ associates with a bundle of digital identities (OpenID, search engine company, web mail provider etc.), which in turn place me into roles like ’emailer’, ‘photo uploader’ that then let me have privileges like ‘send email’, ‘create new album’ etc.
-
‘Employee’ – my persona of ’employee’ gets me a bundle of digital identities that are mostly issues by my employer, some on internal systems, others on Internet connected system with different namespaces…
Hopefully you’re getting the drift by now, and this helps?
Filed under: security | 6 Comments
Tags: digital identity, idm, llp, persona, security, trust
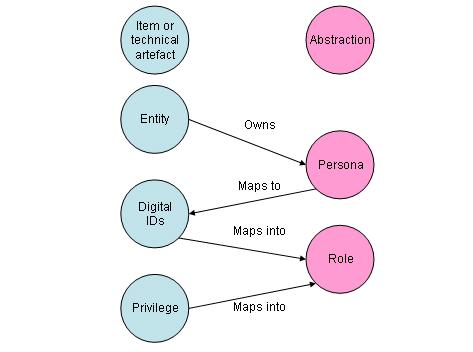
Edited to add labels to the diagram and ensure that the arrows were in the appropriate direction.
Nick Selby raises some great points.
The first is about how persona interacts with device virtualisation so that we can all start carrying less kit around. Device virtualisation allows a single piece of hardware to adopt multiple personalities, and I get to access each of those with an appropriate persona. I can already have a virtualised corporate machine (used by my corporate persona) sat on my laptop (otherwise used by other persona such as blogger, web surfer or whatever). It doesn’t take much foresight to see where this is headed in terms of mobile devices. One of the key facilitating technologies will be soft SIMs (look out for a post soon on telephone numbers as digital IDs), though I do worry that service providers will use the provisioning process for soft SIMs as a way of achieving DRM for mobile phone – we shall see…
I don’t want to distract the debate about defining the abstract concept of persona too much by delving into the implementation issues with limited liability persona (LLP). Just as the crusaders needed to establish something new, legal trusts, to safeguard their property rights it seems that a concept like LLP needs some new legal machinery sat underneath it. I simply wanted to make the point that such machinery doesn’t need to be invented from scratch.
The conversations I’ve been having since making the initial post often wander off into specific federated identity mechanisms, in particular OpenID and Information cards. Since I’ve already used OpenIDs in my examples it should be clear that any OpenID is simply an instance of a digital ID. Information cards are a little more interesting… intrinsically they too are simply digital IDs, but the information card client software provides a friendly abstraction – a picture of a card. So, it seems to me that under the right circumstances information cards, or at least their graphical representations, can be considered to be equivalent to a persona. This impression is further reinforced if you use an information card as the authentication token to one or more OpenIDs (which is nice).
I think I’ll save the RBAC vs. ABAC debate for another post. Suffice to say that role is a pretty easy to grasp abstraction that turns out to be hard to implement, and attribute is I think a harder to describe abstraction that turns out to be easier to implement.
I’d like to offer a tip of the cap to Nick Selby for pointing to this blog entry. It’s quite good, and has helped push my own thinking on this subject along.
I’d say your “persona” definition is just about right. It’s a slice of a person: a facet, a mask they put on, a role they play (and I don’t mean that in a security context). Indeed, personas are going to play a big role in the way technology is provisioned and managed in the future — particularly as we head towards a world where people’s personal and professional (and vocational, etc.) lives blend together. I offer two anecdotes that illustrate why this might be so:
1) I run a security metrics list in my copious free time. A few months ago, one of the members of the list, a security manager for a well-known, slightly old-line Fortune 500 manufacturer asked me what I thought of the idea of giving employees stipends to buy their own laptops. His observation was that a lot of this stuff is like fashion. Allowing employees to pick out their own gear would boost satisfaction. I told him, “it’s a great idea, but you’re going to need to sort out the problem of blended data.” Uncertainty about who owns the data, and how it’s protected, made him a little less enthusiastic. I would suggest that’s only because we’re in uncharted ground — the tools and the legal basis will come eventually.
2) More recently, I took a briefing from a security company that sells smartphone encryption software. I asked them what platforms they supported, and they mentioned IT’s Usual Suspects: Windows Mobile and Blackberry. But they also said they were looking into the iPhone because of the fact that lots of people are buying them. Many of them are taking them to work, too. Some of this company’s customers want to get ahead of this trend, and would like to be able to offer an encryption/wipe option for them. My question to the company was this: “How do you handle the fact that these devices have lots of personal data on them?” Their answer was interesting: “We are looking to carve out a ‘vault’ space on the device for company data.” To me, that’s a tacit acknowledgement that personas will be needed for devices like these. Moreover, it’s probably the camel’s nose in the tent: as category of what we consider “devices like these” expands, we will need technical ways to keep data used by certain personas separate.
Practically speaking, I think virtualization has a role (cough) to play in all this. Rather like Dr. Jekyll walling off Mr. Hyde, why couldn’t owners of personal laptops wall off their work applications, data and communications tools? In-app, even?
Well, these are just thoughts. But something’s got to give. The idea that people are going to carry around two laptops, two cell phones and a BlackBerry isn’t feasible.
Thanks for posting on this, Chris!